Temp Local Admin through MECM Run Script
You’re a Config Manager administrator but your user account
doesn’t have local administrator rights on any of the computers you have to
support. What now?! If only you had access to an enterprise management tool
that could run a PowerShell script on any computer it manages. Yeah, I went
there.
Download Script: https://github.com/rudybankson/Temp-Local-Admin
I wrote a script to add a user to the Administrators group
on a computer for a variable time period. When time expires, a scheduled task
runs once to remove the user from the Administrators group and 10 seconds later
the scheduled task self-destructs in a scene only topped by Tom Cruise in
Mission Impossible. When you run the script, an event is logged in the event viewer
and a Teams channel is notified using a Teams web hook.
DISCLAIMER: This
method of adding a local administrator is far from secure. Unless you have
Group Policy or some other tamper resistant 3rd party tool managing
your Administrator group, your “temporary” administrator could make their
administrator rights permanent.
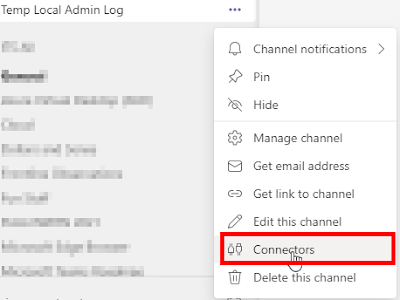
You’ll need to setup a Teams Incoming Webhook to take full
advantage of this script. Make a Teams channel (or use an existing one), right
click on the channel, and click on Connectors.
Find Incoming Webhook on the list and click Add.
Input a name for the webhook and click Create.
You should now see the URL for the Teams Webhook URI. Click
the Copy button and then Done.
Go to \Software Library\Overview\Scripts in your MECM
console. Click Create Script and the wizard opens. Paste the script from my GitHub (IMPORTANT: towards the bottom of the script, you’ll need to replace https://YOUR.URI.HERE with your unique Teams Webhook
URI URL from the step above) into the Script section and click Next.
You’ll now see the Script Parameters step of the wizard. If
you’re a one domain shop or have a “preferred” domain that would be used
commonly, put in a default value for your domain. I like to set the Minutes
default to 15. For demo purposes, I want to minimize the security risk by
setting a maximum value on the time of 120 minutes. Highlight Minutes, click Edit,
set a maximum value of 120, and click OK. Click Next a couple
times and close the wizard when it finishes. Then approve your script and it’s
good to use.
To run the script now, right click on a Device and click on Run
Script.
The Run Script wizard opens where you will select the script and click Next.
The next wizard screen will prompt for script parameters.
Input the domain, the minutes you want the temp local admin access to last, and
the user. On this demo I set a maximum of 240 for the minutes (yes, I know it
was 120 in the above screenshots but I changed it) and when I tried to enter a
value of 500 minutes it shows an error that you must enter a number between 1
and 240, the maximum that I set. Once you have your parameters filled out,
click Next twice and then close the wizard.
At this point you should have received a notification on
your Teams channel. The notification shows some basic information such as
computer, IP, user, and the expiration.
The Event Viewer on the local PC that the script targeted will
have an entry in the Windows Logs > Application log. The Event Source is Temp
Local Admin and the Event ID is 42. The general tab for the
event shows the user that was granted access and the expiration.
The scheduled tasks on the local PC that the script targeted
will have a new task. The task name will be Remove [domain] [user] as temp
local admin. The trigger will be One Time expiring based on the
value you put in minutes when running the script. The trigger “expires” one
minute after the trigger occurs.
The actions tab will show you the Start a program
action running powershell.exe Remove-LocalGroupMember -Group “Administrators”
-Member [domain]\[user].
You can see on the settings tab that the task is set to
delete 10 seconds after it is not scheduled to run again. In other words, 10
seconds after the task expires (back in the trigger section above) then it will
automatically delete itself.
So why use this? I’m remoted onto a computer trying to install a poorly coded program that requires the user to install it, but they need local admin rights to do the install. I want to access the C$ share of a computer I’m troubleshooting to watch MECM client logs real-time or maybe drop some files on it for testing. I want to RDP to the computer and do something requiring admin rights. I want to be able to use Recast’s Right Click Tools to their full potential. So many reasons, no reason to name them all.
As always, feel free to hit me up if you have any improvements
for my script or if you have any other cool things that you make it do on your
own. The possibilities are endless.













Great work! Is there a way to prevent the user from just deleting the scheduled tasks? Like maybe let it be owned by system or something that would make deleting it a litle bit complicated.
ReplyDelete