Java Hunting
Have you ever meet anyone with Java installed across their systems and a clean vulnerability scan? Me neither. I recently set off on a journey to cleanse Java from my environment. The biggest challenge so far has been how to find out who actually uses something that relies on Java.
I have used the System Center Dudes Java Inventory and Metering report for ages, but I wanted to get more data to confirm what I was seeing. My good friends/coworkers over on the security team suggested using Microsoft Defender Advanced Hunting to track down usage of Java. It can do that?!
Microsoft Defender Advanced Hunting is based on Kusto Query Language (KQL) so if you're familiar with Config Manager's CMPivot, you should be able to jump right in and be an Advanced Hunting pro. Advanced Hunting allows you to query the entire life of a computer as far back as 30 days.
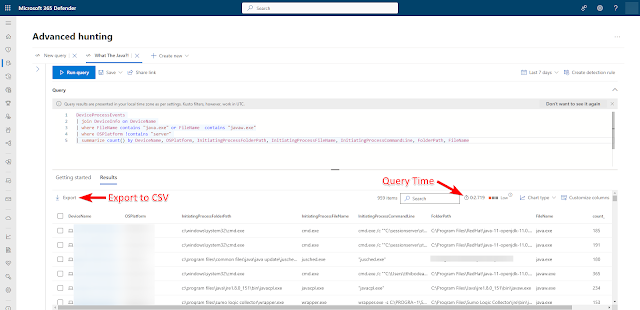
For my Java hunting needs, I wrote a query that is looking for anytime the java.exe or javaw.exe process ran. The query shows me the device name, OS, what kicked off the call to Java, and where Java is actually running from.This query and a couple others I made are on my GitHub at https://github.com/rudybankson/DefenderAdvancedHunting.
DeviceProcessEvents
| join DeviceInfo on DeviceName
| where FileName contains "java.exe" or FileName contains "javaw.exe"
| where OSPlatform !contains "server"
| summarize count() by DeviceName, OSPlatform, InitiatingProcessFolderPath, InitiatingProcessFileName, InitiatingProcessCommandLine, FolderPath, FileName
This query takes about 2.7 seconds to run covering a 7 day period for my fleet of around 20,000 devices. I'm trying to avoid boiling the ocean so I'm taking the results of this list and importing the devices into a Config Manager Device Collection which will be allowed to keep Java for now. If a system isn't in that "keepers" collection for Java, I run a script (from Config Manager either as a package or a Run Script action) that removes Java.
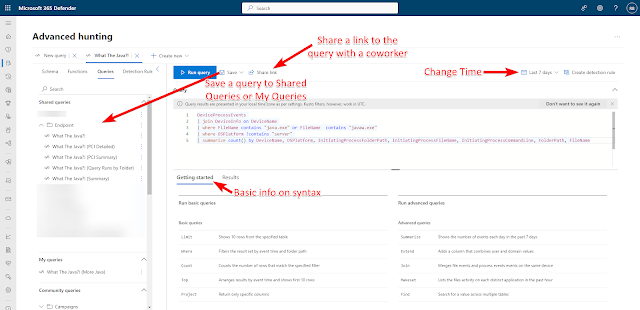
You can save queries you have made to a "My Queries" folder visible only to you or a "Shared Queries" folder visible to others in your organization. If you want to share a specific query with a coworker, there is a "Share Link" button making it easy to ensure they get the right query. You can change the time from the top right of the query to cover as much as 30 days. Basic info on syntax is available in the Getting Started tab.
I have this query along with two others on my GitHub. One of the others is a summary that shows all instances of Java running but it is for the overall environment and not by individual computer. The other of the others is a query that shows you any process run from either of the main Java install folders in Program Files / Program Files (x86). You could easily adapt these queries to find usage data on nearly any application in your environment.
Godspeed on your journey to eliminating Java vulnerabilities in your environment! Happy hunting!

Comments
Post a Comment