HELP, My SCCM SQL DB Filled Up
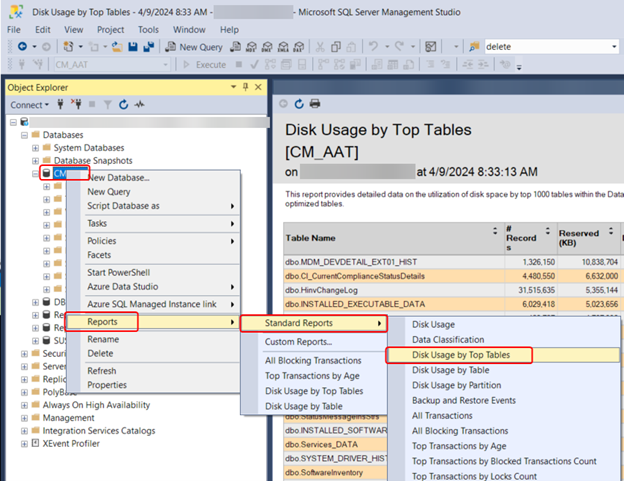
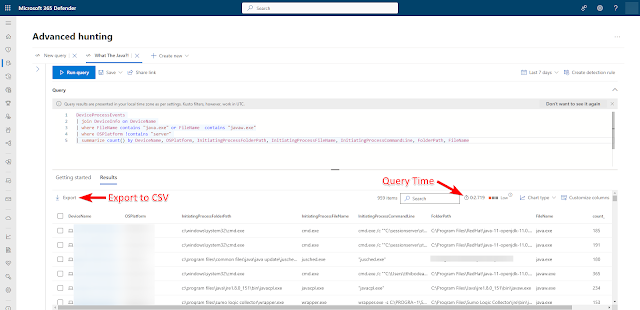
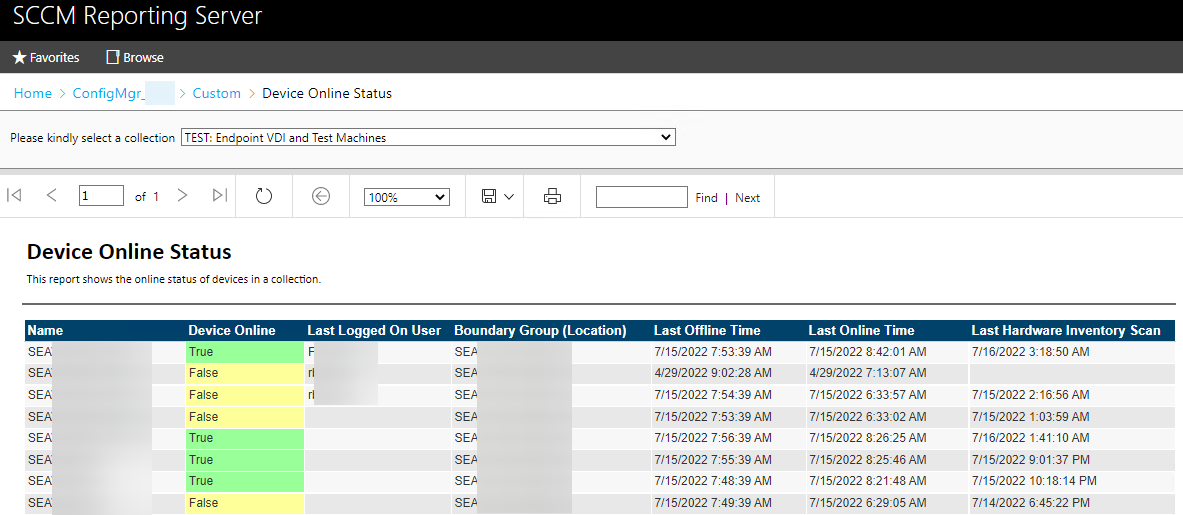
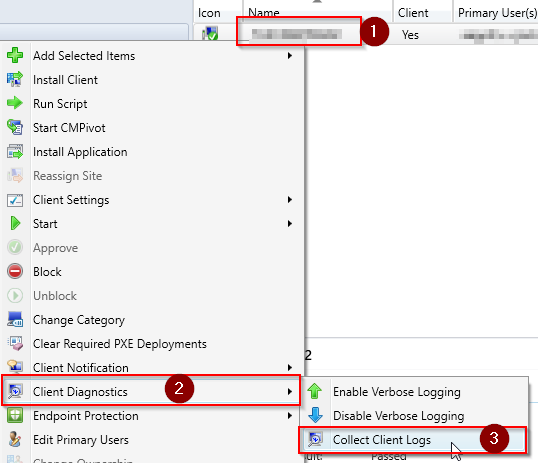
Good morning friend, this is your wakeup call. The SCCM database is growing at 1 GB per minute and you’re about to be out of space. Yes, there are better ways to wake up, like hearing the waves crashing on the beach outside of your tropical hotel room. Our DBA team let us know that the alerting we were getting was spot on, and they had tracked down one transaction in SQL that was running for a very long time. They showed us the details on that transaction which included a client name. We went with our first reaction which was to completely destroy that client install and hopefully stop the bleeding. While that worked, support later told us to just DISABLE the service on the client to retain logging data that would otherwise get deleted. We looked at our SCCM database using the standard reports available in SSMS, specifically the Disk Usage by Top Tables report. The column for Data (KB) is what we care about the most and for dbo.Logs it showed a size just north of 700 GB. To put t